Security at Pathmode.
Robust protection for your data, built on a zero-trust architecture.
Last updated: February 6, 2026
Your data belongs to you
We recognize the sensitivity of research data and guarantee that any data you upload to Pathmode always remains yours.
Guaranteed data confidentiality
Your data will only ever be used to provide you with our services and never for training AI models for other customers.
Defense-in-Depth Architecture
Multiple layers of security protect your data at every stage
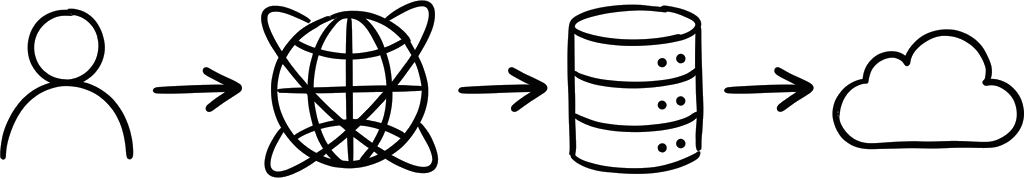
End User
HTTPS / TLS 1.3
Vercel Network
DDoS Protection
Supabase (AWS)
RLS Policies & Encryption
Google Vertex AI
Stateless Inference
Security Features
Comprehensive security measures to protect your data
Encryption
AES-256 Encryption at Rest & TLS 1.3 in Transit
All data is encrypted using industry-standard AES-256 at rest and TLS 1.3 in transit. API keys and sensitive credentials are never exposed client-side.
Authentication
Multi-Factor Security with Strong Passwords
Strict access control: All application access requires a verified account. Anonymous or guest access is strictly prohibited.
Content Security Policy
XSS Protection & Secure Resource Loading
Strict CSP headers prevent cross-site scripting (XSS) attacks and ensure only trusted resources are loaded. All user inputs are validated and sanitized.
Input Validation
Comprehensive Sanitization & Validation
All user inputs are validated for type, length, and format. HTML content is sanitized using DOMPurify to prevent injection attacks.
AI Privacy
Server-Side Processing with Zero Retention
AI API calls are processed server-side with API keys never exposed. AI-generated content is processed without storing your prompts or responses.
Rate Limiting
DoS Protection & Abuse Prevention
API endpoints are protected with rate limiting to prevent abuse and ensure fair usage. Limits are enforced per user and IP address.
Access Control
Row-Level Security & Role-Based Access
Authenticated-Only Access: Zero-trust approach where every request is authenticated. Workspace restrictions ensure complete data isolation.
Backups
Point-in-Time Recovery Enabled
Automated daily backups with point-in-time recovery capabilities for data protection and disaster recovery.
Security Headers & Compliance
Industry-standard security headers and regulatory compliance
Security Headers
- ✓Content-Security-Policy (CSP)
- ✓X-Frame-Options: DENY
- ✓X-Content-Type-Options: nosniff
- ✓X-XSS-Protection: 1; mode=block
- ✓Strict-Transport-Security (HSTS)
- ✓Referrer-Policy: strict-origin-when-cross-origin
Compliance & Standards
GDPR Compliant
Full compliance with EU General Data Protection Regulation
- ✓Explicit consent collection
- ✓Right to access & data export
- ✓Right to deletion (self-service)
- ✓Cookie consent management
- ✓Privacy policy & terms of service
- ○OWASP Top 10 Security Practices
- ○Industry-Standard Encryption
- ○Regular Security Audits
Note: Aligned with ISO 27001 standards; formal certification in progress.
Data Protection & Privacy
Your data, your control
Data Anonymization
Personal data is automatically detected and anonymized before processing. We ensure PII is stripped to protect individual privacy.
Data Residency
Data is stored in AWS regions (via Supabase) with configurable geographic locations. Default: EU-based infrastructure.
Data Retention
You control your data. Delete your account or workspace at any time. Data is permanently removed within 30 days of deletion.
Right to Access
Export your data anytime. Contact us for a complete data export in machine-readable format.
Sub-processors
Trusted partners who help us deliver Pathmode
We work with trusted third-party service providers to deliver Pathmode. All sub-processors are bound by strict data processing agreements.
Google Cloud Platform
Infrastructure and AI services
Supabase
Database and authentication services
Vercel
Hosting and edge network
Vulnerability Disclosure
We take security seriously and appreciate responsible disclosure
Responsible Disclosure Guidelines
- Report vulnerabilities promptly to security@pathmode.io
- Provide detailed information about the vulnerability
- Allow reasonable time for us to address the issue before public disclosure
- Do not access or modify user data without permission
We will acknowledge receipt within 48 hours and work with you to resolve the issue.
Incident Response
Structured process for handling security incidents
In the event of a security incident, we follow a structured response process:
Detection & Analysis
Continuous monitoring and automated alerts help us detect incidents quickly.
Containment & Eradication
Immediate steps to contain the threat and remove it from our systems.
Recovery & Post-Incident
Restore services and conduct post-incident review to prevent recurrence.
Notification
Affected users will be notified within 72 hours of confirmed incidents, per GDPR requirements.
Security Updates & Maintenance
Continuous improvement and proactive security measures
Dependency Management
We regularly audit dependencies for known vulnerabilities and apply security patches promptly. Automated dependency scanning helps identify issues early.
Security Monitoring
Continuous monitoring of API usage, authentication attempts, and system logs helps us detect and respond to threats in real-time.
Regular Audits
We conduct regular security reviews and code audits to identify and address potential vulnerabilities proactively.
Security Contact
Get in touch with our security team
For security-related questions, concerns, or to report a vulnerability, please contact our security team:
For security vulnerabilities and incidents
Response Time
We aim to respond to security inquiries within 48 hours